What are the possible usages of a cryptographic certificate?
About
A certificate may have one or more several usages. This articles list them and show you how to discover the usage also known as certificat purpose.
The usage (key_usage and extended_key_usage) are stored in the certificate as extensions.
List
Key Usage
A certificate can be used for one or more of the below usage category known as KeyUsage (KU, or id-ce-keyUsage) 1) :
| Name Identifier | Name for Human | Description |
|---|---|---|
| digitalSignature | Digital signature | To add a signature to a message |
| nonRepudiation | non-repudation - the message cannot be denied from having been sent | |
| keyEncipherment | To encrypt a key | |
| dataEncipherment | To encrypt data | |
| keyAgreement | For key exchange | |
| keyCertSign | Certificate signing | To signed a certificate |
| cRLSign | CRL signing | To sign a certificate revocation list (crl) |
| encipherOnly and decipherOnly | To only encrypt or decrypt |
The usage name is the name used by openssl.
The key usage usage is explained in the x509 specification section-4.2.1.3.
Extended Key Usage
The ExtendedKeyUsage (or id-ce-extKeyUsage) 2) is another field that defines more precisely the keyusage by defining the purpose.
The list below is non-exhaustive 3).
| Name | Object ID (OID) 4) | Description |
|---|---|---|
| serverAuth | id-kp-serverAuth | SSL/TLS Web Server Authentication. |
| clientAuth | id-kp-clientAuth | SSL/TLS Web Client Authentication |
| codeSigning | id-kp-codeSigning | Code signing (Signing of downloadable executable code) |
| emailProtection | id-kp-emailProtection | E-mail Protection (S/MIME) |
| timeStamping | Trusted Timestamping (Binding the hash of an object to a time) | |
| msCodeInd | Microsoft Individual Code Signing (authenticode) | |
| msCodeCom | Microsoft Commercial Code Signing (authenticode) | |
| msCTLSign | Microsoft Trust List Signing | |
| msSGC | Microsoft Server Gated Crypto | |
| msEFS | Microsoft Encrypted File System | |
| nsSGC | Netscape Server Gated Crypto |
The key usage usage is explained in the section-4.2.1.3 of the x509 specification 5) where you can see also which key_usage are also required using them.
See
The key_usage and extended_key_usage are stored in the certificate as extensions.
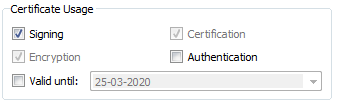
gpg
This is a snaphsot of gpg where we can see the usage.
PorteCle
With portecle, you can see the keyUsage and extendedKeyUsage in the extensions.